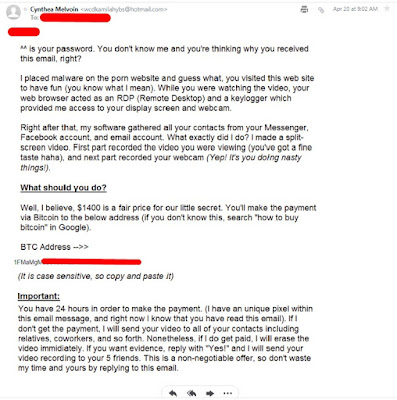
 |
| This is a sample of what users are receiving in email |
Click on the above picture to enlarge so you can read it. It's harmless or we wouldn't have posted it here.
If you are not accustomed to seeing an email like this, it is possible that you got one but it went to your SPAM folder. Emails like this will go to your regular inbox if your email provider recognizes something that you have in common with the sender.
The content is almost always a screenshot, a tip-off that it's not legit and a good email provider will disable the images so your device isn't compromised. The sender uses screenshots because it is easier for him to do mass mailings and to make you give up after the first attempt to copy paste it into a search engine to authenticate it.
There are two kinds of readers: The first reader recognizes the letter as a scam and is confident in deleting it because they don't use (or have) a webcam, don't use Facebook/Messenger, and don't watch videos on their computer.
The second reader is the one who reads it with a guilty conscience and falls for it hook, line and sinker - making themselves a perfect target.
This email is a "sextortion" attempt.

For those who can't read the text on the above picture, here's the short version.
The email states:
"that malware was placed on a porn website that "you" visited (to have fun) and while you were watching the video, your web browser acted as a Remote Desktop and a keylogger, which allowed (the sender) to see your display screen and webcam. (The sender's) software gathered your contacts from Messenger, Facebook, and email. (The sender claims to have) made a split screen video of the porn video and of you while you were watching it doing a nasty act. (The sender says) that $1400 is a fair price to keep your secret and payment is to be made by 24 hours in Bitcoin to the BTC case sensitive address provided. (The sender claims to be able) to see when you have read the email. If you send payment, (the sender) says the video will be erased "immidieately" But if you want evidence, you can REPLY with "Yes!" which will make (the sender) proceed to send your video to 5 of your friends. The offer is non negotiable so don't waste my time and yours by replying to this email."
Your first instinct after seeing your password at the top might be to quickly change your password - which never hurts, especially if you are still using the same password on one or more accounts. We have always strongly discouraged our readers against using one password on multiple sites because if you are ever hacked or if a massive security breach happens where mainly passwords were stolen, you can be attacked on all of your accounts at the same time and there's nothing you can do about it. Even if you slightly change the same password by adding some numbers or symbols after it, you are still using a similar password. Please don't do that. Always use completely different passwords on different sites.
Whether the claims in the email are true or not, no matter how pissed off you are - DO NOT REPLY. The first time you reply to the email, one of two things will happen: the message will either bounce back as "not deliverable" OR you will become a bigger victim (target) than you are now.
Replying to an email like this is foolish because you most likely are doing battle against a computer-generated program which sent the same message to thousands of people at one time. Each one will be customized to the target with a different password that could be a current password (or part of a password) or one that was used in the past.
This email was sent to Geek Admin Maggie King which, because of her security settings, was automatically sent to her SPAM folder where it belongs. Maggie said she found it because she routinely goes through her SPAM folder before emptying it to make sure important stuff wasn't sent to SPAM in error which her email provider has done in the past with legitimate emails.
So, why did you get the email in the first place?
We seriously don't believe every recipient was watching a porn video. The mention of a porn video was used as a vehicle to perpetrate extortion. The real reason you got the sextortion email with the outdated password at the top is most likely because the sender is working off old information that was acquired during a breach from some time ago.
But how did they get your password? It is possible that your credit cards, medical records, or banking records could have been hacked.
But it is a better bet that your Facebook or your email provider (Yahoo, Outlook, AOL, Gmail, Apple, etc) was hacked.
Admin Maggie King uses Yahoo for her email provider and Yahoo was hacked in August 2013 which they did not report to the public for three years, until 2016. The stolen data included names, dates of birth, email addresses and physical addresses, telephone numbers, passwords, security questions and answers, and contents of some emails where users emailed their newly changed password to themselves for safekeeping.
In 2016 when Yahoo first alerted the public of the August 2013 hack, they said, "only 500 million users were hacked" which was not true. In December 2016, Yahoo confirmed that the accounts of over one billion users had been hacked.
In 2017, Verizon became Yahoo's new owner/parent company and shortly after they also verified that Yahoo's August 2013 hack affected every user who had a Yahoo account at the time which, Verizon said, was nearly one billion users. This number also was not exactly true.
Even more unsuspecting users were affected because Yahoo also owns Tumblr, Fantasy and Flickr. In 2017 Yahoo revealed that 2 billion users of those websites were also hacked bringing the total number to 3 billion accounts whose personal information is in the wind, up for sale on the Dark Web.
Hacked information is best used while it is "fresh" when no one knows they've been hacked. Because Yahoo didn't report it in 2013, and because users were not aware their details were hacked, the information remained fresh for a very long time.
Yahoo said they didn't report it because they didn't want to lose the trust and confidence of its users.
They lost more by not reporting it.
Who knows? Maybe the hackers were holding something else over Yahoo's head to keep them from reporting the hack.
In August 2016, Yahoo said they were aware that hackers were advertising the sale of stolen passwords of 200 million Yahoo accounts on the Dark Web. They told users to change their passwords, use different passwords on different platforms and to consider using an Account Key
To add insult to injury, Yahoo was hacked again in 2014 - which they did not disclose until 2016 after they told the public about the August 2013 hack. The new 2014 hack affected another 500 million users, mainly users of newly made Yahoo accounts. Yahoo believes that the same hackers were behind both attacks.
To notify users, Yahoo placed a small obscure post on Tumblr saying Yahoo was taking steps to secure the affected accounts and was working closely with law enforcement to get to the bottom of the hack.
People trust Apple and think Apple can't be hacked. But they can. In August 2018, Apple reported that they were hacked by an Australian teen who hacked into Apple's private servers over a long period of time and stole 90GB of private information.
The password at the top of Maggie's email was part of one she had been using back in 2013 when Yahoo was hacked. This means the hacker sat on the stolen information for so long after he got it in 2013 (or he sold it on the Dark Web and the new owners also didn't use it in a timely manner) that this rendered her password information useless.
So that all will not be lost, when you are talking about the potential profit to be made off the private information of 3 billion users, the new owner of the hacked information is not about to give up. Judging by this email, he is still trying to make a buck off it.
Here's our take on the "sextortionist."
The sender is most likely a desperate semi-literate second rate wannabe hacker who thinks the information is far valuable than it is, who hopes to make a few bucks by sending sextortion letters in bulk by using an old app that obviously didn't come with a proofreader, waiting for a reply from some guilty, unsuspecting, totally uninformed email recipient who will do anything to keep his secret from being revealed, and will make the sender rich beyond his wildest dreams by sending $1400 in Bitcoin!
It's been five years and according to the latest reports, Yahoo still doesn't know how 3 billion accounts were hacked nor exactly who the hackers were.
Good hackers have been notoriously successful at not getting caught. It is our opinion that Yahoo will never know the identity of the hackers.
As long as there is information available to be sold, and as long as some unsuspecting user believes the sextortion emails, the hackers are going to win in more ways than one.
UPDATE: April 17, 2019
In March 2018, Yahoo was ordered to pay out a total of $117.5 million by a federal judge to reimburse $55 million to victims for out of pocket expenses, $24 million for two years of credit monitoring, up to $30 million for legal fees and up to $8.5 million for miscellaneous expenses.
On April 17, 2019, more names were added to the Customer Data Security Breach Litigation list for reimbursement and out-of-pocket expenses which you can read here.
In March 2019, US Prosecutors charged two Russian intelligence agents and two hackers with one of Yahoo's two breaches. No trial date has been scheduled.
To check if your email address was included in a data breach, go to this site https://haveibeenpwned.com
Enter your email address to get a list of data breaches where your email address was acquired by hackers
If you live in the USA, you can file an internet crime complaint at https://www.ic3.gov/default.aspx
Share our posts with your friends so they can be up to date too. Thank you.










