- A separate class-action lawsuit was filed against GitHub on August 1, 2019, for negligence and violation of the federal Wiretap Act (for allowing hackers to store sensitive user information on their servers) and California civil code for failure to remove personal information belonging to Capital One users that had been exposed on their site for nearly 3 months. This lawsuit, which also levies charges against Capital One, contends that GitHub's website actively encourages hacking.
Today, we are outlining some of the points in Capital One's FBI complaint which you can read later when you are done reading here.
THE DEVIL IS IN DETAILS
The Capital One breach and the subsequent investigation had some details that were not made public on July 29, 2019 but were later released via news media and in the class action lawsuit transcript file.
At the end of this post, we are also giving you a link to join the class-action lawsuit. Use the criteria below to see if you qualify to be included.
 |
| Do you qualify to join the class-action lawsuit against Capital One? |
CAPITAL ONE'S PRESS STATEMENT
According to Capital One's press statement on their website, they claimed that no Social Security numbers, login information or passwords were compromised, except for the 140,000 Social Security numbers and 80,000 linked bank accounts they identified in their original statement.
So even though the hack allegedly compromised the personal data of over 100 million customers, Capital One is saying that nearly all of the other user Social Security numbers and login data was tokenized and that they are sure it was only these 140,000 Social Security numbers and 80,000 linked bank accounts who were affected.
Our first question is: How the heck do they know this for sure?
- According to their statement, they didn't even know they had an 'intrusion' in March 2019 when Paige Thompson hacked their files not once but several times.
- They also claimed they didn't see a direct message that was sent to their email in June 2019 from someone warning (or threatening) that the stolen information was going to be exposed soon if they didn't act. When the information was exposed, Capital One still did not act on it.
Our second question is:
- How did the customers with the exposed 140,000 Social Security numbers and the 80,000 linked bank accounts get so unlucky as to not be tokenized so that their data was the only data to be compromised "for sure" out of over 100 million customers? Why wasn't their data tokenized like it was for all other customers?
Ok, enough about that. After the horse already escaped from the barn, Capital One's next step was to take care of the fallout.
Their primary way to do that was to downplay it by calling it an "incident" as opposed to a hack or a breach.
- The change in wording was possibly a last ditch effort to save some face.
THE DIFFERENCE BETWEEN A BREACH AND A HACK
- A breach is when data or files are unintentionally left unsecured and vulnerable to hacking, as a result of a bad actor's malicious activity or from negligence.
- A hack occurs when cyber-attackers purposely access to compromise a company's software, hardware, networks or service components to steal information or to hold for ransom. This is what happened with Capital One.
There doesn't seem to be much difference between the two, at first reading.
- But when you read the definitions more closely, you could say that a little bit of both can be applied to Capital One.
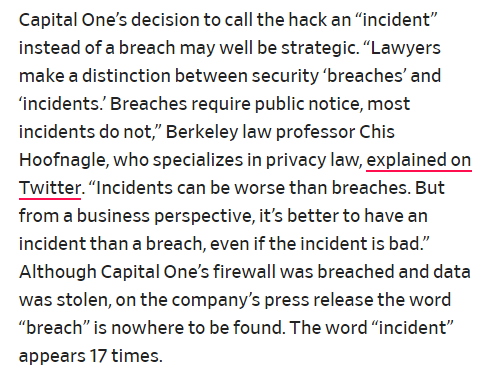 |
| Berkeley Law Professor Chris Hoofnagle on Twitter at https://twitter.com/hoofnagle/status/1156200937330839553 |
Capital One's choice use the word 'incident' doesn't smooth anything over. In our view, it all comes down to using a term that makes Capital One look more like a victim in place of a term that likely makes them look worse than they already do.
- For Capital One and their supporters to say, "Capital One suffered an "incident" sounds a whole lot better and less accusatory than to say "Capital One had a breach," or "Capital One was hacked."
However there are many people who don't think hacked companies are victims at all. In conversation, whether it is said with regret or with scorn, you will primarily hear: "Capital One got hacked." It's just human nature.
This "incident" is not a clear cut situation as Capital One would like the public to believe.
Here is a screenshot and link to Capital One's press release on their website. Notice the wording we pointed out in blue boxes. Capital One emphatically states that no other customers were compromised.
Although her identity was known at the time but unclear whether she was charged yet, instead of referring to her as "the hacker," they referred to her as "the individual."
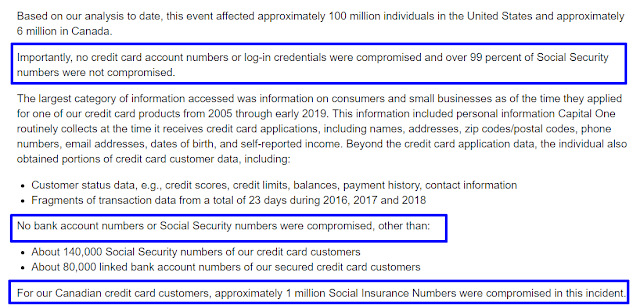 |
| Capital One's press statement |
http://press.capitalone.com/phoenix.zhtml?c=251626&p=irol-newsArticle&ID=2405043
WHO IS AFFECTED
Although companies are not required to notify their account holders of a breach or a hack, the best way to keep current of such events is your local news, your internet's home page and by ongoing observation of user activity on your accounts. Capital One did notify some of their customers early on.
Until stated differently, this hack affects Capital One account holders - past and present - who live in the United States and Canada, particularly Florida and California. Users need to be aware of the following:
- the extent of the breached data,
- when Capital One learned of the breach,
- Capital One's actions to attempt a cover-up,
- your benefits of joining a class-action lawsuit.
Don't be so quick to dismiss this by thinking that the lawsuit requires your presence in court or that you don't stand a chance of getting anything out of it.
Although Capital One is giving compromised users two full years of free credit monitoring, the class action lawsuit states that the least you can get is 6 months of free credit monitoring protection (a savings of about $99) or $125 (+ or -), depending on the number of participants in the class action who receive payments.
You may qualify if you:
- Live in California, Florida, parts of the United States and Canada as stated in the file Page 9, lines 2 through 27 who provided personal information to Capital One and whose personal information was accessed, compromised or stolen by an unauthorized individual or individuals in the data breach announced by Capital One on July 29, 2019.
- paid money to repair your credit or for credit monitoring,
- already had in place (or have since paid for) identity theft insurance either monthly through Capital One credit card services or through another company,
- noticed fraudulent charges on your credit card statements
- were charged interest or finance charges on fraudulent charges.
- suffered psychological stress or illness due to this hacking event (requires documentation, for example, billing of professional services) .
- were contacted by Capital One and told that your account was compromised
If any of the above circumstances apply to you, or if you have another reason that you think makes you eligible, then you should complete the form so a lawyer from the firm that is handling class-action lawsuit can contact you to discuss it.
FYI
The breach not only affected personal and business account holders who used Capital One as their bank. It also affected anyone who completed applications to apply for a credit card or other services for the 14 year period from 2005 through 2019.
- This includes both approved and denied credit applications.
 |
| Capital One statement regarding consumers And small businesses |
If you own a business or if you had business accounts with Capital One where your customer data was made known to Capital One, there could be a domino effect if your passwords or data was not encrypted or tokenized.
Cyber-security experts advise changing passwords as well as your diligent and continued observation for malicious activity.
CREDIT CARD DISCLOSURE
Because Capital One collected personal and financial data to process each application, the class action lawsuit charges that, because they were hacked, Capital One is in violation of their own disclosure statement which is provided to all applicants, both by phone and on paper.
 |
| Capital One is charged in the lawsuit with violating their Disclosure Contract |
SO, DID CAPITAL ONE ATTEMPT TO COVER UP THIS 'INCIDENT'?
Whenever a hacked party is aware of the occurrence of a malicious event or intrusion, then makes an attempt to hide it, or to work with, or to coerce another actor to remove or hide it from public view, this can constitute a cover-up.
When Capital One learned that their stolen files that were exposed on GitHub detailing how their customer data was hacked, Capital One's only concern was to request GitHub to remove just those parts of the files that showed "how" they were hacked.
- Capital One demonstrated very little or no concern for their customer data because they didn't request the file, in whole or in part, to be removed from GitHub.
- There is a very small possibility that Capital One's concern was for other companies who could be hacked by bad actors using the same method as shown in the exposed file on GitHub. If that were the case, one would logically think that Capital One's next action would have been to request GitHub to remove the entire file, then immediately follow up by making a report to the FBI. But they didn't do that, so this possibility is not likely.
- GitHub allowed the data lay exposed on GitHub's site for almost 90 days. GitHub certainly knew it was sensitive information belonging to Capital One's database because they publicly commented that they saw no reason to remove it since there were no exposed names, birthdates or Social Security numbers. If they knew what information was not in the file, then they knew that the file was on their site all that time.
The following screenshot is from the top class-action lawsuit website which states:
 |
| GitHub's Statement |
DATE OF AWARENESS
While reading the details of the lawsuit complaint and various news releases as they evolved, it appears that a direct message was sent to Capital One that warned or threatened to release the stolen information to the public. If this is true, then this is when Capital One's "date of awareness" changed from July 17, 2019 to a undisclosed date in June 2019.
This screenshot is from the FBI complaint on page 11. The reporting source is Capital One.
https://www.justice.gov/usao-wdwa/press-release/file/1188626/download
The following screenshot is from a news report at
https://telegraph.co.uk/news/2019/07/30/capital-one-data-breach-exposes-100-million-customers-us
 |
| From The Telegraph, July 30, 2019 |
Capital One knew of the seriousness of this event after the June 2019 email that threatened the files were going to be exposed soon. Since it wasn't a done deal as of June 2019, Capital One could have acted on this at that time instead of waiting another six weeks before notifying the FBI and the public.
One can only wonder if GitHub would have removed any part of the stolen file at all, had they not been contacted by Capital One to remove only the part of the file about how Capital One was hacked.
DETAILS OF THE HACK
The hacker, Paige A Thompson, who goes by the screen name "erratic" on Twitter, is a former software engineer who worked for Amazon's Cloud Services based in Seattle, Washington.
- Her position at Amazon is important now, but in July 2019, the news reports gave no job specifics, only that she had worked for Amazon.
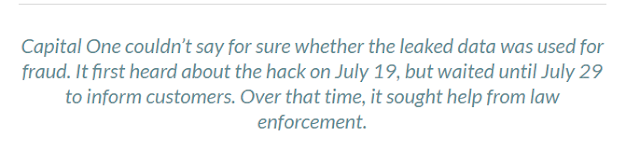
On July 29, 2019, Capital One notified the FBI and the news media that they had experienced a data breach in their system which they said they became aware of ten days before, on July 19, 2019. Evidently, this was not true.
In news reports and documents that have since become public, their date of awareness appears to have been in June 2019 with the first email contact that their user data was about to be exposed. Essentially it was being held hostage without a stated ransom amount.
However, the data was already exposed on GitHub sometime in early April 2019 so the email threat was long after the data was public on GitHub.
As for the age of the stolen information, we, as members of the public, assumed the hacked information was from the current year so that people who had dealings with Capital One from years ago did not become concerned.
- What was little emphasized in the initial July 29, 2019 filing was that the March 2019 hacked information included files that dated back 14 years (from 2005 to 2019) of personal and business accounts (credit card applications that were both approved and denied), corporate accounts and anyone who used (or applied for) Capital One loans or bank accounts.
 |
| From the FBI report |
The FBI reports show that Capital One was contacted a second time by email on July 17, 2019 to say that their leaked data was already posted on GitHub, a web hosting site. But as of July 17, 2019, Capital One still didn't notify the FBI or their account holders that they had been hacked. They waited 12 more days until July 29, 2019, which allowed the stolen information to stay exposed on GitHub, to be further exploited and potentially purchased by bad actors.
However the public was led to believe that the data was only on GitHub dating from July 17 when Capital One received email notification that the files were already posted on GitHub.
GitHub was aware that the files were on their site due to their refusal to take them down by stating that there weren't any exposed Social Security numbers and other personal information to warrant removal. This demonstrates that GitHub had knowledge that Capital One's files were on their site for a lot longer than 12 days.
According to the FBI report and class action lawsuit complaint, Capital One waited over a month to reveal the breach. They received at least two direct messages between June 2019 and July 2019 and they were aware of a Twitter user known by the screen name "erratic."
This changes Capital One's "date of awareness." Even though "erratic's" June 2019 messages to Capital One warned that the stolen data was going to be distributed, it implied that the files were not yet exposed. The hacker lied because the data had been exposed on GitHub since April 2019.
Capital One still did not act on any of the information.
By ignoring and not immediately reporting they had been hacked, Capital One further deprived their customers for a full month of taking other precautions (for example: buying identity theft insurance or creating stronger passwords). This caused a delay in Capital One start of two years of identity theft insurance which large corporations offer to their users after a hack.
For the time between June 2019 and July 2019, people who had applied for Capital One credit cards most likely would have chosen not to do so if they were aware of the hack, thereby safeguarding their own data.
On July 29, 2019 when Capital One went public with the breach date of March 2019, they said the stolen data included "names, birthdates, and Social Security numbers" of over 100 million account holders in the United States and 6 million in Canada. But they backpedaled on that later by stating much lower numbers.
By doing this, when customers like us heard this in news reports, it sounded like it wasn't that bad of a hack because Capital One said in their press statement that most customer names, birthdates and Social Security numbers were not part of the stolen data.
Although the public knows they cannot change their names, birthdates or Social Security numbers, they also know that there's no sense in getting upset about something that can't be changed. At that point, the hack was blown off by most people as minor.
According to the class-action lawsuit, the details of the stolen data was:
Capital One said the stolen data also included credit scores and linked credit card information - other credit cards or bank account information that users kept on file with Capital One as a way to pay their bill.
The way that Paige A Thompson hacked Capital One should be of some concern, but to date, we haven't seen anyone who addressed it.
Amazon offered storage space much the way an apartment building owner offers his building's apartments as rental space to tenants.
Capital One redesigned the space so it could hold more files, much the way a renter would paint and decorate their rented apartment space.
Amazon had a master key, so to speak, to access just the Cloud (their property), which they also provided to their employees so they could access the Cloud, perform routine maintenance, etc. This access did not necessarily include the files contained on the Cloud. This is similar to the way a building manager employed by an apartment building owner has a master key in the event of a fire or medical emergency where he would give attention to just that section of the apartment but not to the renter's personal belongings inside the apartment.
Paige Thompson, as an employee of Amazon, gained access into the Cloud server owned by Amazon but rented by Capital One, just as a building manager would gain access to an apartment in a building she managed.
With knowledge gained as a former Amazon software engineer employee for Amazon's Cloud Services, Paige Thompson hacked into Amazon's Cloud Server which suggests that the original way to access might not have been changed since the time she was an employee.
Amazon says they have no liability here because the space they leased to Capital One was fully controlled by Capital One. Amazon's Cloud Server only provided them with storage space. Amazon might be held responsible for the actions of their employee who gained unauthorized non-emergency access to rented space, depending on whether she was still an employee or a former employee.
Whether or not Capital One rented space or controlled the compromised server, Amazon owns the Cloud and their employee hacked it, so the court may decide that Amazon will share liability.
EXIT QUESTIONS:
In our opinion, Capital One is as guilty as GitHub for allowing the stolen data to remain exposed and threatened from June to the last week of July, 2019.
It doesn't matter whether it was ransomed or just threatened to be exposed. Capital One knew about it and that alone is cause to fine them and for them to pay restitution to users.
Who do you think should be held financially responsible?
Should it be Capital One who controlled their own data security on a Cloud Service which was owned by Amazon?
Should it be GitHub, who knew the data was exposed on their website for 90 days and at Capital One's request, chose to hide some details of the hacking instead of reporting it and completely taking the file down?
Should it be both companies?
Should Amazon be named in the lawsuit since they provided the space for data storage on their Cloud Server?
The Class Action lawsuit is open for account holders to join.
Once the court makes a determination, the court will decide whether to place fines against the guilty parties and in what amount.
The extent of the financial liability will depend on the economic and psychological impact that the hacking event had on individual Capital One account holders whose data was compromised and how many people in the class filed for financial compensation.
You can read the complete court document here.
https://www.dropbox.com/s/cjdflk7rh4z8ery/TZ_GitHub_CapitalOne_FINAL_Complaint_8_1_19.pdf?dl=0
Please share our posts with your friends so they can be made aware of this class-action lawsuit and the details of this case. Thank you.
 |
| Details of Capital One data breach |
Capital One said the stolen data also included credit scores and linked credit card information - other credit cards or bank account information that users kept on file with Capital One as a way to pay their bill.
Originally, the reports said only Capital One users was affected by the breach. But the lawsuit states that the data of more than 30 companies who did business with Capital One had also been breached.
The way that Paige A Thompson hacked Capital One should be of some concern, but to date, we haven't seen anyone who addressed it.
Amazon offered storage space much the way an apartment building owner offers his building's apartments as rental space to tenants.
Capital One redesigned the space so it could hold more files, much the way a renter would paint and decorate their rented apartment space.
Amazon had a master key, so to speak, to access just the Cloud (their property), which they also provided to their employees so they could access the Cloud, perform routine maintenance, etc. This access did not necessarily include the files contained on the Cloud. This is similar to the way a building manager employed by an apartment building owner has a master key in the event of a fire or medical emergency where he would give attention to just that section of the apartment but not to the renter's personal belongings inside the apartment.
Paige Thompson, as an employee of Amazon, gained access into the Cloud server owned by Amazon but rented by Capital One, just as a building manager would gain access to an apartment in a building she managed.
With knowledge gained as a former Amazon software engineer employee for Amazon's Cloud Services, Paige Thompson hacked into Amazon's Cloud Server which suggests that the original way to access might not have been changed since the time she was an employee.
Amazon says they have no liability here because the space they leased to Capital One was fully controlled by Capital One. Amazon's Cloud Server only provided them with storage space. Amazon might be held responsible for the actions of their employee who gained unauthorized non-emergency access to rented space, depending on whether she was still an employee or a former employee.
Whether or not Capital One rented space or controlled the compromised server, Amazon owns the Cloud and their employee hacked it, so the court may decide that Amazon will share liability.
EXIT QUESTIONS:
In our opinion, Capital One is as guilty as GitHub for allowing the stolen data to remain exposed and threatened from June to the last week of July, 2019.
It doesn't matter whether it was ransomed or just threatened to be exposed. Capital One knew about it and that alone is cause to fine them and for them to pay restitution to users.
Who do you think should be held financially responsible?
Should it be Capital One who controlled their own data security on a Cloud Service which was owned by Amazon?
Should it be GitHub, who knew the data was exposed on their website for 90 days and at Capital One's request, chose to hide some details of the hacking instead of reporting it and completely taking the file down?
Should it be both companies?
Should Amazon be named in the lawsuit since they provided the space for data storage on their Cloud Server?
The Class Action lawsuit is open for account holders to join.
Once the court makes a determination, the court will decide whether to place fines against the guilty parties and in what amount.
The extent of the financial liability will depend on the economic and psychological impact that the hacking event had on individual Capital One account holders whose data was compromised and how many people in the class filed for financial compensation.
You can read the complete court document here.
https://www.dropbox.com/s/cjdflk7rh4z8ery/TZ_GitHub_CapitalOne_FINAL_Complaint_8_1_19.pdf?dl=0
This link will take you to the questionnaire for the class-action lawsuit. Once you complete the form, you will be contacted by an attorney only if you qualify to join the lawsuit.
Please share our posts with your friends so they can be made aware of this class-action lawsuit and the details of this case. Thank you.

