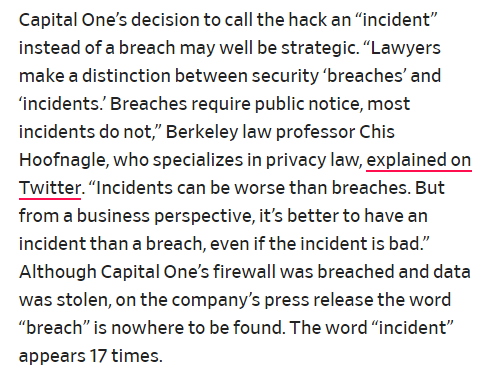
A flash drive, also known as a thumb drive, a USB stick, or memory stick, is a convenient plug-and-play device that is slightly larger than the average human thumb. Their primary function is to store files, videos and photos so you can take them with you when away from your own computer, plug the drive into the USB port of a different computer to display, share and transfer files, videos, documents or photos to one or more users.
 |
| Example of flash drive size |
We use multiple flash drives to back up documents, photos and important files on our hard drive. Each flash drive is labeled according to project and each time we update a file, we plug in the flash drive, save a copy to it and a copy to the hard drive.
How to Find It On Your Computer
When inserted into a USB port of a computer, that computer's operating system recognizes it as a removable device and identifies it with a drive letter. The storage capacity of flash drives ranges from 2 megabytes up to 1 terabyte. New technology in 2023, 2024, and 2025 promises to increase the storage to 2 terabytes.
Their primary function is to store files, videos and photos but if you delete files or reformat the flash drive to remove fragments of files, then the device will degrade and will no longer be reliable.
Password or PIN Protected
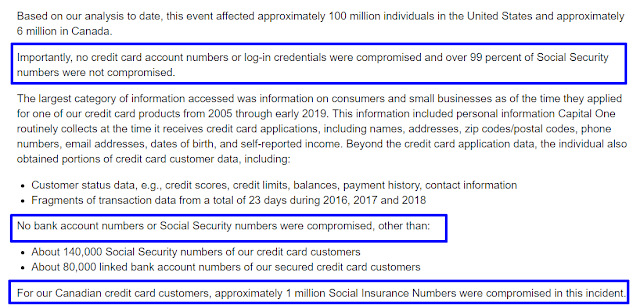
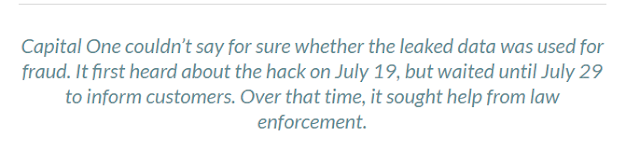
Sensitive information stored on flash drives can be protected with a password or a PIN. Given the thousands of security breaches in recent years, many people saw their personal information stolen by bad actors who used it to apply for bank loans and credit cards. It makes good sense to add a password or a PIN as an extra layer of protection to safeguard your stored information. If someone does not have the password or PIN, they can't access the info on that flash drive.
This 'N That
Internet - Flash drives do not require an internet connection.
Cloud - No information is stored on a cloud unless you choose to use it that way so the flash drive acts as a go-between.
There is no need to save files to your computer if you are saving them to a flash drive. We choose to do it as insurance against loss.
If you share a computer with someone, flash drives hide your info from prying eyes.
Transfer Speeds
When it comes to flash drives, size matters and so does the transfer speed. Low cost flash drives usually have slow transfer speeds such as USB 1.0 low speed which transfers about 1.5 megabits per second (Mbps). These are pretty much obsolete now except on ebay or small town pawn shops.
A USB 1.0 high speed transfers at about 12 megabits (Mbps) per second. For USB 2.0 high speed has a maximum transfer rate of 480 megabits per second. For 3.0 Super Speed, the data transfer rate is about 5 gigabits per second (Gbps) and 3.1 Super Speed Plus has a transfer rate of about 10 Gbps.
Ready Boost
For older PCs with low memory or smaller hard drives, you can use a flash drive to install Ready Boost, an app that speeds up slow hard drives but you have to use 3.0 flash drive to get adequate speed.
Miscellaneous About Flash Drives
- No batteries required.
- No rebooting required (of PC or flash drive).
- Flash drives have no moving parts, however, they can physically get lost. Keeping them on a key chain attached to your belt has been a trend, however if your keys become unhooked from your belt and get lost, then you have lost your flash drives as well.
- If you do not have a lockout feature on your computer or if you choose not to use a password to lock it, you can install a Windows app on your flash drive that acts like a special Unlock key (some app examples: Raptor, Serpent, Flash Security, Predator, Lock USB, USB Lockit, Ease US, Lock My File). Plug in the flash drive while working at your computer. When you are doing working, remove the flash drive, the screen goes dark and your device stays locked until you return. Reinsert the flash drive and it wakes up your screen.
If you use the protective cover or case that is sold with your flash drives, then the device will hold up well against minor mishaps.
Information can stay stored on a flash drive for years. When ready for use, it adapts to any operating system because the stored information is not dependent on the operating system in which the files were created.
Flash drives are not immune to malware. If you insert it into an infected device, your flash drive can become infected too. The best you can do at that point is to trash the flash drive because transferring info from an infected flash drive to a new flash drive will likely transfer the malware too.