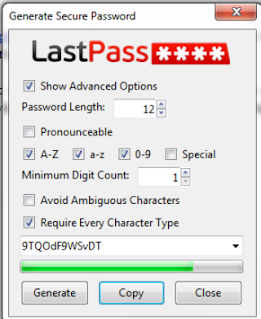
As much as you have read that you shouldn't use your passwords more than once, it's human nature. Everyone does it.
By the time you are done reading all three parts, if you don't want to change the passwords that you use on your websites, then we can only assume that:
- you feel 100% safe because you have chosen the perfect passwords OR
- you already use your passwords only once, OR
- you are lazy, OR
- the job is too big because of how many passwords you have to change, OR
- you don't care about your online security
 |
| Hackers are able to hack so many accounts because users choose weak guessable passwords |
When users think that their chosen password is the absolute best password ever that no one will ever guess, this makes them feel so secure so that they are more likely to use it on more than one website.
The longer they go without an intrusion or a hacking scare, the more likely they are to not change them for long periods of time because they assume if nothing bad happened all this time, then there is no reason to change their passwords.
The Top Reasons Why People Re-Use Passwords
People re-use passwords for a variety of reasons, the most common one is that it's easy to remember. The average online user:
- changes their password every three to five years
- will not make up a new password and instead will re-use one that they have used in the past
- often keeps a list of five or more passwords they have used for years and they recycle them whenever they change their password
- likes to pick a new password from something old, something that is familiar
Humor us and take a look at these lists of passwords and password formulas.
If your password (or a variation of it) is on any of the lists, and if you have used it on more than one website, then you seriously need to consider changing it or, at the very least, enhancing it to make it stronger.
These lists are commonly used passwords as defined by experts which are the most hackable. We admins have seen these passwords used by hacked accounts that we have helped to recover.
In no particular order, both with or without capitalization and with or without a mixture of numbers, letters or symbols:
Examples of Bad Passwords
Geez, I guess you're thinking that there's nothing left.
There is, but you have to put on your thinking cap.
Before we go further, we want to point out the obvious and that is how a hacker gets any of the above information in the first place.
As much as we don't like to blame the distraught Facebook user who has been hacked, it's usually his own fault that he has been hacked because of his privacy settings, or lack thereof. Leaving personal information exposed - like a present city of residence, locations of past schools jobs - these give the hacker enough information to steal the user's whole identity.
Remember: Facebook doesn't "need" to know where you went to school, where you work, and the names of relatives, which by the way, they connect to you with 'live' links to their Facebook accounts. Facebook will ask, but they don't need it.
So take a look at your Facebook settings, and hide or remove any information in the bio, introduction, "about" section, timeline posts, and comments that provide personal information so that a hacker can pick you out among a list of people with your same name.
- the word "password" in any format
- username or myusernameis
- 00001234
- yournamehere
- password123456
- qwerty
- letmeinnow
- asdf_jkl;
- numbers in sequences: 987654321 or 123456789
- abc123
- dragon
- admin1234
- starwars
- helloitsme
- mypasswordis
- JFK11221963
- 11111111
- charlie tuna
- youvegotmail
- barack obama
- the word "welcome"
- donald trump
- mactheknife
- facebook1234
- hilary clinton
- q1w2e3r4t5y6
- abcdefg or abcd1234
- the words "iloveyou"
- the words "your name here"
- city of birth (belonging to you or a family member) and a birth year
- a pet's name, no matter if it is your pet or not
- your first, middle, maiden or divorced name or an immediate family member
- your child's name - first, middle or last
- a favorite sports team's name or mascot's name
- dates that are important to you with or without a year - an anniversary, a birthdate of you, a child, a spouse, pet's birthdate, a relative's death date, a graduation date
- a favorite holiday of the year
- a favorite vacation spot
- your honeymoon destination
- your present city
- a present or former street address of yours or a close family member
Geez, I guess you're thinking that there's nothing left.
There is, but you have to put on your thinking cap.
Before we go further, we want to point out the obvious and that is how a hacker gets any of the above information in the first place.
As much as we don't like to blame the distraught Facebook user who has been hacked, it's usually his own fault that he has been hacked because of his privacy settings, or lack thereof. Leaving personal information exposed - like a present city of residence, locations of past schools jobs - these give the hacker enough information to steal the user's whole identity.
Remember: Facebook doesn't "need" to know where you went to school, where you work, and the names of relatives, which by the way, they connect to you with 'live' links to their Facebook accounts. Facebook will ask, but they don't need it.
So take a look at your Facebook settings, and hide or remove any information in the bio, introduction, "about" section, timeline posts, and comments that provide personal information so that a hacker can pick you out among a list of people with your same name.
How People Find You
When anyone wants to know information about you, the first thing they usually do is check to see what you have exposed on social media. They will check for accounts on Facebook, Instagram, Tumblr, and other social media accounts. Then they will type your name in Google's search box with your zip code or city.
You would be amazed at the wealth of information in the search returns. Sometimes there's stuff you thought no one knew because you kept it private.
When anyone wants to know information about you, the first thing they usually do is check to see what you have exposed on social media. They will check for accounts on Facebook, Instagram, Tumblr, and other social media accounts. Then they will type your name in Google's search box with your zip code or city.
You would be amazed at the wealth of information in the search returns. Sometimes there's stuff you thought no one knew because you kept it private.
The results also give them links to your social media accounts and any websites or blogs you might own, have contributed to, wrote as a guest blogger, or left comments.
There is one site, Radaris dot com that provides far too much information, including your current phone number and email address. Their terms of service states that the info can only be removed from their site by you after you prove your identity to them.
A word to the wise. You might be motivated to follow their process to prove your identity because your eye is on the prize of having your information removed from their website. But you have to keep in mind that these websites also sell information which means you don't know how many times your info has been sold or how many sites already have it.
Don't get conned by believing they will remove your information from their site because sometimes the hoops you have to jump through to get them to do that are not worth it. I looked into it to see what they would require as proof and I chose not to follow through because proving my identity meant uploading my photo driver's license. That is the one piece of information you should be guarding with your life because it irrevocably links your information to the picture on Google and other search engines as well as facial recognition programs.
Since the photo driver's license was one piece of information I pretty much knew they did not have, I wondered what they would be comparing it to in order to verify my identity.
So guard it with your life and don't give it to any website so they can further link you to their search results or sell it as a "premium" with other information.
Besides, if they do remove your information from their site, there's no guarantee they won't put it back on their site again, so tread lightly.
Within the search results, there are always advertisements but they are usually advertisements with an ulterior motive. While most users skip over the ads, sometimes there's a fact in one of the ads that might catch your eye enough to raise your curiosity. That's because the ads are geared to show certain key facts about you that are absolutely true, to persuade a user to click on it to investigate. Nine times out of ten, it is a con, but most people are curious and will click on the ad.
Within the search results, there are always advertisements but they are usually advertisements with an ulterior motive. While most users skip over the ads, sometimes there's a fact in one of the ads that might catch your eye enough to raise your curiosity. That's because the ads are geared to show certain key facts about you that are absolutely true, to persuade a user to click on it to investigate. Nine times out of ten, it is a con, but most people are curious and will click on the ad.
Once you do, the webmaster or website moderator can see who you are, where you are located and all the information that is attached to the account you are using.
If you are new to their website, a login box will popup to ask you to create an account. It goes directly into their database and is compared against any info about you that they already have and if they see anything different, they will use it to update their records.
This is another reason why we always teach that you should Google yourself once or twice every month to see what Google is telling searchers about you. If there are any surprises, you might be able to take action.
After the ads, the rest of the results will include tracking sites like ancestry.com, truthfinders.com, radaris.com, and intellius.com. These sites provide a lot of information about you and they didn't even have to hack you to get it. It is all available online for free - compliments of the Freedom of Information Act (which in our opinion is one of the worst infringements on our privacy).
This is another reason why we always teach that you should Google yourself once or twice every month to see what Google is telling searchers about you. If there are any surprises, you might be able to take action.
After the ads, the rest of the results will include tracking sites like ancestry.com, truthfinders.com, radaris.com, and intellius.com. These sites provide a lot of information about you and they didn't even have to hack you to get it. It is all available online for free - compliments of the Freedom of Information Act (which in our opinion is one of the worst infringements on our privacy).
This law allows anyone to see key details about your life such as your credit rating, important dates like birthdates (with or without the birth year) email addresses, former residences, etc. for not only you but sometimes your immediate family members too, your past and present employment, schools attended, and graduation years, if you have a mortgage and with whom, etc.
This law is how most of those sites collected your information so they could use it to populate their websites. Without it, they'd have to resort to other tactics to gather the information or they wouldn't have a website anyone would want to use.
The search results from Googling your name are similar to the information that we showed above for a password formula:
- your birthdate, some portion of your social security number with the rest "blacked out;"
- any other names you now use or have used in the past, your credit rating, dates like birthdate or just the birth year, your schools and graduation years, your mortgage company, if you have a car loan or lease and whom you pay;
- your marriage and divorce date;
- names and/or birthdates of your children, their ages, their names and addresses of spouses or significant others where they have had mail sent to their addresses;
- your former and present phone numbers and mailing addresses; (Two sites have a list of all your neighbors, their addresses and their phone numbers)
- your former and present employment including dates and addresses;
- if you are affiliated with any websites.
A hacker doesn't need all of the information found in search results. He can target his next victim with minimal information such as:
- your birthdate OR
- a phone number (as seen on your Facebook account)
- your present location with or without an actual street address (a zip code or city is enough) OR
- the name and location of your high school.
All hope is not lost. You do have some options to protect yourself which we will explain in the next two parts of this series.
Please share our link with your friends so they can enjoy our websites too. Thank you for stopping by.